Microsoft Outlook Elevation of Privilege Vulnerability
On 14.03.2023, Microsoft announced the “Elevation of Privilege in Microsoft Outlook” vulnerability.

The vulnerability is tracked as CVE-2023-23397 and its exploit causes password hashes to be stolen.
The vulnerability is in such a critical state that the exploit code has already been released and the
vulnerability has been exploited.
It is a fact that we are almost racing against time against vulnerability. For this, it is of great importance to take the necessary actions without wasting time.
We have prepared a small guide for you.
You can reduce the impact of the attack by applying the following list to your organizations.
Looking at the details of the vulnerability, attackers can exploit the vulnerability by sending MAPI-capable messages containing UNC routes to an SMB share (TCP 445) under their control.
The vulnerability affects all versions of Microsoft Outlook, but not Android, iOS, or macOS.
Affected Systems
- Microsoft Outlook 2016 (64-bit edition)
- Microsoft Outlook 2013 Service Pack 1 (32-bit editions)
- Microsoft Outlook 2013 RT Service Pack 1
- Microsoft Outlook 2013 Service Pack 1 (64-bit editions)
- Microsoft Office 2019 for 32-bit editions
- Microsoft 365 Apps for Enterprise for 32-bit Systems
- Microsoft Office 2019 for 64-bit editions
- Microsoft 365 Apps for Enterprise for 64-bit Systems
- Microsoft Office LTSC 2021 for 64-bit editions
- Microsoft Outlook 2016 (32-bit edition)
- Microsoft Office LTSC 2021 for 32-bit editions
IoC’s
-
Recommended Solution(s)
- Install the Exchange Server updates released this month without delay. If you have missing Exchange Server updates, complete them without wasting time.
- Make Office updates without wasting time.
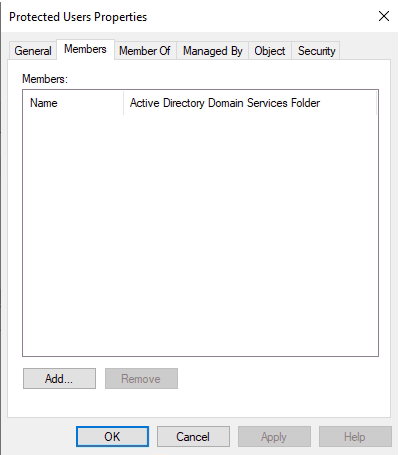
- Sensitive accounts(accounts with access to critical systems) that we call critical accounts that are members of groups such as Domain Admis, Schema Admins, Enterprise Admins; add it to the Protected Users Group and you will have encrypted traffic with kerberos.
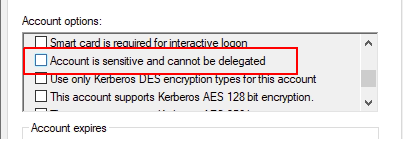
- Sensitive accounts(accounts with access to critical systems) that we call critical accounts that are members of groups such as Domain Admis, Schema Admins, Enterprise Admins; go to it’s properties and tick the “account is sensitive and cannot be delegated” option. Thus, delegation cannot be assigned to these sensitive accounts.
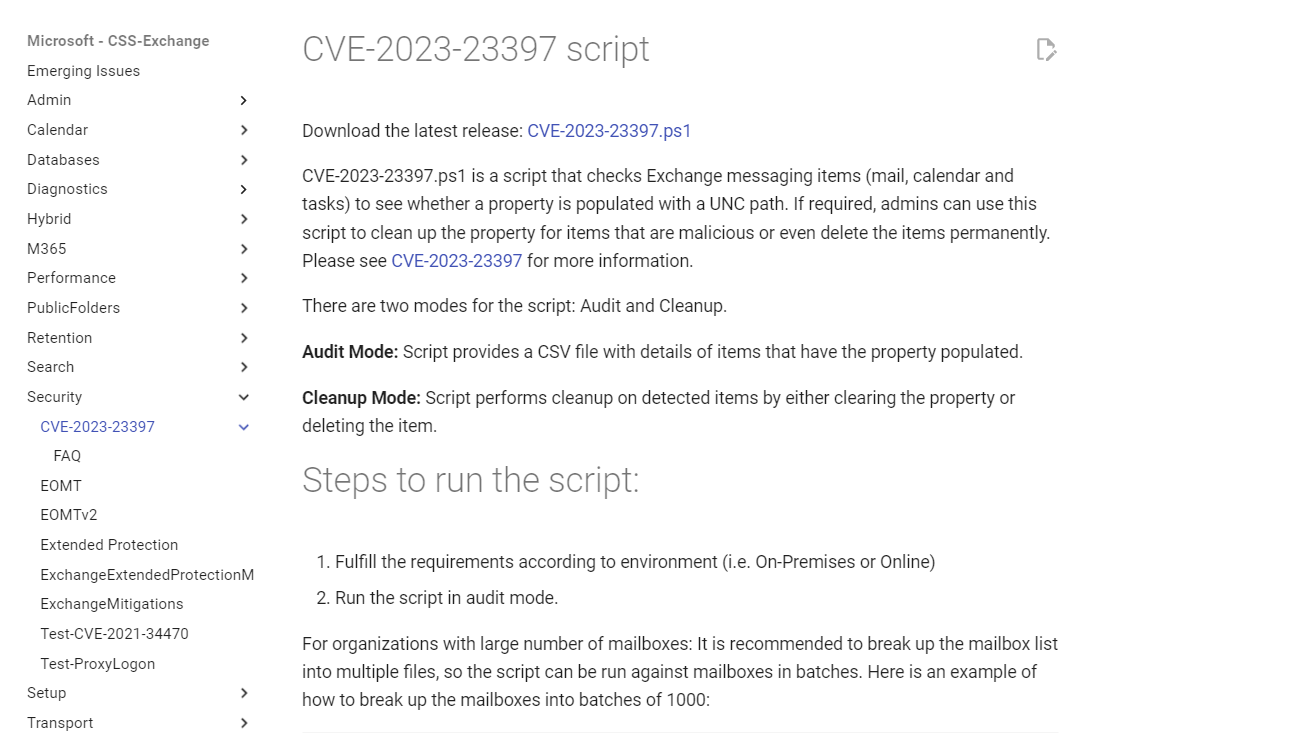
- To detect and clean Microsoft's email accounts affected by this vulnerability; Provide the controls by using the script it publishes.
CVE / CWE
CVE-2023-23397
Related Website(s)
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-23397
- https://microsoft.github.io/CSS-Exchange/Security/CVE-2023-23397/
* CVSS 3.1 score (out of 9.8) 9.1/“high”
* Those between 9.0-10.0 are considered as “critical” vulnerabilities.
Current Security Vulnerability Reports
İSTANBUL
+90 216 504 53 32
Aydınevler Mahallesi,İsmet İnönü Cadddesi,Küçükyalı Ofis Park A Blok,No:20/1 Maltepe İstanbul
ANKARA
+90 312 235 44 51
VULNERABILITY NEWSLETTER
You can register to our newsletter on the home page to be instantly informed about security vulnerabilities.
