SolarWinds Sunburst Attack Campaign
In the leak report announced by FireEye in December 2020, it was reported that the leak was carried out through a module containing a backdoor on the platform called SolarWinds Orion.

FireEye identified this trojanized backdoor as UNC2452, named SUNBURST, while that backdoor was named Solorigate by Microsoft.
Orion software updates, released between March and June 2020, have been found to provide attackers with surveillance and backdoor code that allows attackers to execute commands.
Affected Systems
The following components with SolarWinds Orion installed and running on versions 2019.4 HF 5 or 2020.2 HF 1 have been reported to be affected.
- Application Centric Monitor (ACM)
- Database Performance Analyzer (DPA)
- Integration Module* (DPAIM*)
- Enterprise Operations Console (EOC)
- High Availability (HA)
- IP Address Manager (IPAM)
- Log Analyzer (LA)
- Network Automation Manager (NAM)
- Network Configuration Manager (NCM)
- Network Operations Manager (NOM)
- User Device Tracker (UDT)
- Network Performance Monitor (NPM)
- NetFlow Traffic Analyzer (NTA)
- Server & Application Monitor (SAM)
- Server Configuration Monitor (SCM)
- Storage Resource Monitor (SRM)
- Virtualization Manager (VMAN)
- VoIP & Network Quality Manager (VNQM)
- Web Performance Monitor (WPM)
Recommendation
- In particular, it is recommended to upgrade to the current fix (2020.2.1 HF 1) as soon as possible and follow SolarWinds publications for 2020.2.1 HF 2 correction.
- It is recommended to restrict local administrator accounts on SolarWinds servers.
- It is recommended to prevent Solarwinds servers from accessing the internet.
- It is recommended to change the passwords of the accounts that can access SolarWinds servers.
Links
- https://cyber.dhs.gov/ed/21-01/
- https://www.solarwinds.com/securityadvisory
- https://github.com/fireeye/sunburst_countermeasures
Actions by Barikat MSOC After Vulnerability Release
- Contact has been established with all customers who have SolarWinds infrastructure
- Necessary follow-ups on deepweb and dark web were made on behalf of our customers.
- Our constantly updated IOC list has been entered into customer threat detection systems.
- Connections were taken under control at every possible point, and process-related consultancy was provided to our customers.
Related Signs Lists (IOC List) SHA256
- dab758bf98d9b36fa057a66cd0284737abf89857b73ca89280267ee7caf62f3b
- 32519b85c0b422e4656de6e6c41878e95fd95026267daab4215ee59c107d6c77
- eb6fab5a2964c5817fb239a7a5079cabca0a00464fb3e07155f28b0a57a2c0ed
- c09040d35630d75dfef0f804f320f8b3d16a481071076918e9b236a321c1ea77
- ac1b2b89e60707a20e9eb1ca480bc3410ead40643b386d624c5d21b47c02917c
- 019085a76ba7126fff22770d71bd901c325fc68ac55aa743327984e89f4b0134
- ce77d116a074dab7a22a0fd4f2c1ab475f16eec42e1ded3c0b0aa8211fe858d6
- d0d626deb3f9484e649294a8dfa814c5568f846d5aa02d4cdad5d041a29d5600
- 53f8dfc65169ccda021b72a62e0c22a4db7c4077f002fa742717d41b3c40f2c7
- 019085a76ba7126fff22770d71bd901c325fc68ac55aa743327984e89f4b0134
- 292327e5c94afa352cc5a02ca273df543f2020d0e76368ff96c84f4e90778712
- c15abaf51e78ca56c0376522d699c978217bf041a3bd3c71d09193efa5717c71
MD5
- 02af7cec58b9a5da1c542b5a32151ba1
- 08e35543d6110ed11fdf558bb093d401
- 2c4a910a1299cdae2a4e55988a2f102e
- 846e27a652a5e1bfbd0ddd38a16dc865
- b91ce2fa41029f6955bff20079468448
- 4f2eb62fa529c0283b28d05ddd311fae
- 56ceb6d0011d87b6e4d7023d7ef85676
IP List

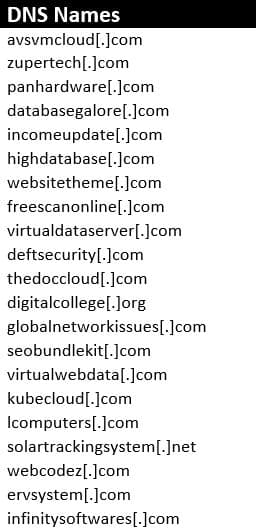
DNS Names
Current Security Vulnerability Reports
İSTANBUL
+90 216 504 53 32
Aydınevler Mahallesi,İsmet İnönü Cadddesi,Küçükyalı Ofis Park A Blok,No:20/1 Maltepe İstanbul
ANKARA
+90 312 235 44 51
VULNERABILITY NEWSLETTER
You can register to our newsletter on the home page to be instantly informed about security vulnerabilities.
