StrongPity Watering Hole
Strongpity isimli grup Türkiye ve Suriye’yi hedef alarak watering hole tekniğiyle zararlı yazılım bulaştırarak bilgisayarda bulunan verileri komuta kontrol sunucusuna göndermeye çalışmaktadır.

Strongpity isimli grup Türkiye ve Suriye’yi hedef alarak watering hole tekniğiyle zararlı yazılım bulaştırarak bilgisayarda bulunan verileri komuta kontrol sunucusuna göndermeye çalışmaktadır.
Çözüm / Öneri
Aşağıdaki IOC listesinin desteklenen tüm güvenlik ürünlerinde engellenmesi önerilmektedir.
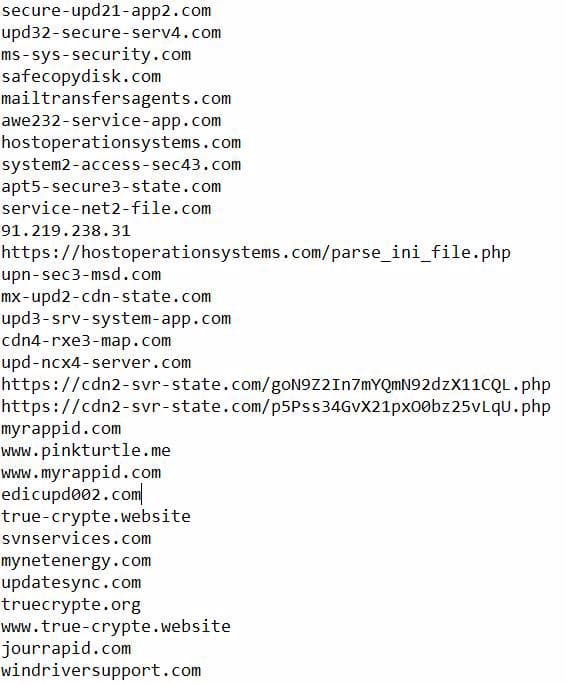
DOMAIN/URL
IMPHASH
- 7e5ef0f67c9691533818d048499b5083
- 8abe3681c11e209ff85599f5e699bd77
- b996e2c3977a7044670484c0428d059e
- 40972f3608f18dcf148832b47c7524d6
- 5fa2da673f6659ad061ecc63793cb430
- 90570395bfeb43df5c7a271296b7c409
- b8a776afbe9999cb74349d365654ecec
- 8263eabf0c88e0ff484d4b184535386e
- 19aab448aea5b08b156c7070cd50e863
- 511f4e5cf1e4bf26001be1cad53c9833
- 5f832e44f10de876e667dbfbcb653ef9
- 3e412aae37cfc3cdd7732c914db43671
MD5
- e43d847aeda31ddd94fec050f4e887a9
- 4f6d3ef07f3cbeb61d038f339440c32c
- dd0cdbf78966a41e064daf490f95ceaa
- 0a3c01ccd948ec12d75cb591ab320887
- c5c5a751c63ef4cdd6bfd34780068f00
- b7677e42852e9b8a3857476fda540224
- 73faf13cbf33e00d730a6b9a00cb277e
- 900d937455c62807fb4b0b0000142d37
- 2d0f3620bbea500e7cfab2f28fb10e9b
- 05e373b594b9995dbc876fba21e1a082
- d4057c628387f461b15ec7ad78de6ca1
- faa1ba96a35259af5cdaf48ea76ad984
- 06752c080a5c00baf971243be65a49b8
- 476e0ed5ba666132ef574f47d7d6b511
- 32a2b332fed353408e2d3b13af6ebfba
- 6dc0a580fad115a741ff6779ffbf3569
- be6f2a03dfddbaf1166854730961d13c
- 08d971f5f4707ae6ea56ed2f243c38b7
- 5f8dd1a37ad2b36b178777d6bbf8a35b
- fa90508007b94a4dbfeb8b48d5443ec8
- f36e67109ae368c9db109d0a41b5817c
- f344da38958dbc730ddebc10660cd451
- e80d8a0c35133f7485d8e87ade903919
- e436e849d9496ef3f651c1904786c78f
- df0045bd4168893922480f7ccb29860a
- d7ec065cc3f563928504f80692578d2f
- be8a344487bcfea66de8e0f0f14d869e
- a5ae6e0d74052d4f889f2538fdd7cb9b
- 2041cc8de9dab93b44434d7f748c63ad
PEHASH
- 4ba78c8e572992a28978e61a03c497ce7847012b
- 827efdfd14ef7646a0530df3923a8b0007cb72ef
- 6cccb0f7a972faccd71928782711153cd015fc3d
- 63c0256c60e4aac29a75ef73022826b517413bc1
- df17ac16f9e8141ebf943000b88103c8524e757a
- 285c2e4f9025024c488c769d527c6037aa8f2f33
- 01ac0c056a17506d59da77b3353da8099fe1cdfb
- abeb59bbe3fce538a653cb5c4364ac7414d2499d
- adea4bd67c448a610cb69a406a7ba5551dfc5525
- 4ff1c64c0f82169698ba480520dffcc442f55e58
- 258538b85eee6afcbcbb0e6337e7c8425a7ed1fb
- 03668c8299e661643eead669e9e9edc01ab2b636
- 18cd08f19282c6cfba216da8ff7fc6edcd3fc0fd
- c12c46473b8e5770baad6dbcb7d51f2e19e2bb85
- 7f2906ebe4a51871692015d5fc526446025d783e
- 0b9055135eeb6dfbd5fe44a102634d26e63dc44a
- b2a1f2bd22f1bd44ed89f4556fdedab43c344d96
- b91b8238ba9ee289312e15a9287f0d8439a1e1e4
- a4fdd463b35627a18b76a11d2b7963c25b15844d
SHA1
- 63ba0b08a52e881ff82862853e45bd572853093c
- 908342c749f8c5970e5c6a57be16057ac69a31c6
- 526e1892c2e72ac6b431975da3f8fc989c9ce751
- 6025590495f99bdd12afe9227ec6dcb6b7a68ebe
- d7cfa28a32c2949f091d7193991f394010f1ecd8
- f328c56c052b6ce1e742d4135df03b8c2e780646
- 43a147b085c305f0cce9fe9a332e645e3cce8de1
- 6ba2eea1ff76f8efda8555b7597a629f54b6b276
- 5900eaec5c34a96bbddcb4fb52c5eb852aa4340c
- 9626caac889c062f55b43475484870d5e6751cee
- 368fcaaad87f28e2ab2552dc47b701f3b49b02c0
- 9302b21b03b452007fab6f62adc0d703edc0f81f
- 33c77f4e017fce4fc25809433b58dce27e2f8bfc
- 6a8d2aa39dcf9dd90dd2c4fa11e1bc3a485fff91
- 4540f094d76c5165c7edc0a4c9479cd69888ba2c
- e554db589ba7ec2dc33218949922ac65a07f1e42
- f8009ef802a28c2e21bce76b31094ed4a16e70d6
- e17b5e71d26b2518871c73e8b1459e85fb922814
- a0437a2c8c50b8748ca3344c38bc80279779add7
- 76fc68607a608018277afa74ee09d5053623ff36
- 87a38a8c357f549b695541d603de30073035043d
- 8b33b11991e1e94b7a1b03d6fb20541c012be0e3
- 9f2d9d2131eff6220abaf97e2acd1bbb5c66f4e0
- eb4e1e24712d9d1f495f7464ff162d2c0aace91a
- 0f22427a5229a89ea2ce134cf6e42d6bfe782aa9
- 76826cc65a8c9f72ddeb9b850a5701b185a5de29
- 17e8293634723da61b2ce78a028097476e51ff00
- 7047ed9ae510377f4625db256e52af02694ef153
SHA256
- 79f02a935266a6a8322dec44c7007f7a148d4327f99b3251cba23625de5d5d5e
- 55e83292bd9a1f843639bfb98648a40b931a9829d62e6b23904034c417ffa430
- 2b62a469fa9737dabc52840a741a7d71c86c74bd6909c30cb481e2d66e0df75e
- 6f0b9fdc7edf43a9d1262263320e623a7e2b349f54185491262fe5184413222f
- b1916e7de11e87fa45c222d0532955e781f6695ae0ee15775894d3b3aa72ba98
- 11849a6fcb76267676532422db4e9bf4f5c8c525fea0d950f844736bedb8b53e
- 2c3b3c085b3992ab105bbc4696391f4f81374c54bb8966e53d2b2de8b7648681
- 92ff23ab81cc20c4916441547745f336cf612c21a049cdcbb01f11d83a40979e
- d77901484e91445d8d11b82ff487b9e56b48930fe3086e5858ea754e9f490c1f
- 2ee74ceaa5964cf223aefb3cf4e0c25ea96c7d4bc0eba48439716e763d2f3837
- 91e20fb663b1809279666fb1e7ef7bd8da42ae51e0c05b51515ba851e2a991ac
- c2c333a5f46eb5894f05f3323ab8aea87b3c2e9ba0221c28dcf46b0842592ac6
- 5b5b0a0ff8e5bdf11657e0134a638a818e31af9517e5feffea247eaa2660ee23
- 521c43c7c01eeb68b2bbb3daaad376d3902a264820e016bb5dd6738e842f331c
- 33eb8f1175416cfbe7aa1490232f5af0ff92b981609634033af0598ce16e4a68
- 821c643002e1eed1a5bc7cb3d15be6df5f7a4b9cb4c938d0008827a3cc29b0b0
- 462e85023952d23b74d697911653604b40497424e7a6fe505366addae6c375f7
- 57da6fa244402a7fe5d4f8f8abf2acbc08db3817faee93dd8ccdc8a2a3554245
- 0ef8d249a2e8cb096b69c7f2cae46a073681bd43fcabc9c50eb5df454c71baea
- 2d3151aaa1467d92a783e76dbfe65adb6d7d5d896d9daeb16e97dd106521654f
- c43ea98bf86791d6f05c21edde4e26eaad2e52fbd7f396bbe9079b41b8fcebfe
- 18c0b5d81afcd601aaf30871c6c3ee0d2f0328bb2381a8a0e34bb60e9862b4cb
- 5ac23fc5e6ab0543da88f1b92327a7b3a644d1eebac8ed4d80d45a8d5d07b994
- 2f98ac11c78ad1b4c5c5c10a88857baf7af43acb9162e8077709db9d563bcf02
Ek Bilgi
Güvenlik Zafiyet Bildirimleri
İSTANBUL
+90 216 504 53 32
Aydınevler Mahallesi,İsmet İnönü Cadddesi,Küçükyalı Ofis Park A Blok,No:20/1 Maltepe İstanbul
ANKARA
+90 312 235 44 51
ZAFİYET BÜLTENİ
Güvenlik zafiyetlerinden anlık haberdar olmak için ana sayfadaki bültenimize kayıt olabilirsiniz.
